Online security is something that should get everyone’s attention. Threats exist all around us: ransomware, viruses, spyware, social engineering attacks and more. There’s so much you need to know to keep your […]


Online security is something that should get everyone’s attention. Threats exist all around us: ransomware, viruses, spyware, social engineering attacks and more. There’s so much you need to know to keep your […]

Everyone has Wi-Fi. We all expect to see it wherever we go, and most of us have more than one Wi-Fi-enabled device. Grocery stores, fast food restaurants – even your mechanic has […]

Limited wireless networks are just what they sound like: small networks with limited range that cannot handle the demands of, say, the entire population of a large high school full of students, […]

Apple’s newest software update has arrived, and it’s already making an impact in how effectively users manage their smartphones. iOS 12, which comes preinstalled in the iPhone XS and iPhone XS Max, […]

Are You REALLY Secure? Follow This Checklist To Know For Sure When everything is going well, the last thing you want to do is think about what will happen when something […]
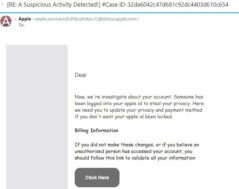
There’s a new Gift Card scam going around that has already cost consumers lots of money, frustration, and headaches. Here’s how it works. You’ll get an email from a friend or relative […]

Considering Working With An Email Marketing Solution To Help Grow Your Business? Email marketing plays a critical role in helping you to reach the right people and expand your client base, share […]

Creating and maintaining electronic health records enables caregivers to manage various aspects of patient care more effectively. However, storing and handling patient information (on-premise or in the cloud) comes with the responsibility of implementing robust healthcare data security measures. At Kraft Technology Group, we provide technology solutions that medical practices or healthcare-related enterprises like yours may leverage to maintain, process, share, and secure electronic protected health information (ePHI).
It came to light yesterday, through a suit filed in federal court, that the email of an Aspire Health employee was hacked this month and that lead to 124 emails being forwarded […]

According to Statista, there were 184 million ransomware attacks in 2017 and the average ransomware demand is over $1,000. Individuals, organizations, and companies have fallen victim to these attacks. Most people recognize […]

Kraft Technology Group today announced that it has become a Champion of National Cybersecurity Awareness Month (NCSAM) 2018. It will be joining a growing global effort among businesses, government agencies, colleges and universities, associations, nonprofit organizations and individuals to promote the awareness of online safety and privacy.

A compromised endpoint gives hackers everything they need to get a foothold in your security network. Once there, they can steal data and potentially hold it for ransom. That’s why it’s so […]