Cybercriminals will take advantage of any crisis, including the COVID-19 pandemic. CISA’s latest alert is warning healthcare organizations of increased cybercriminal activity.


Cybercriminals will take advantage of any crisis, including the COVID-19 pandemic. CISA’s latest alert is warning healthcare organizations of increased cybercriminal activity.

This spring, Microsoft is transitioning the Office 365 suites that many small and medium businesses rely on to Microsoft 365. While this will bring some level of change for most companies that recently used an Office 365 or Office 365 ProPlus suite, the overall impact of the change is expected to have minimal material effect on business operations and bottom lines.

There has been a significant increase in coronavirus-themed cyberattacks as more workers are being forced to work from home. This makes these companies an easy target for hackers -- and the financial ramifications for your business can be significant.

As more businesses and schools move to Zoom for videoconferencing, harmful disruptions are emerging. Here’s how to protect your company from zoombombing.

Did you know 60% of ALL backups are incomplete - meaning only partial backups are created? And to make matters worse, 50% of data restores can fail altogether.
Kraft Technology Group’s Don Baham recently joined the StratoZen team on a webinar to talk about COVID-19 and the effects it has had on the MSP and IT support community as a whole.
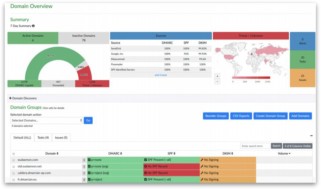
(Domain-based Message Authentication, Reporting and Conformance) is a domain-based email control. Email domains are a shared resource within most organizations with use spanning from employees to entire departments, external parties that send email on behalf of the organization, and the organization’s own Internet-facing applications.

We’re All Adapting to New Ways of Learning, Collaborating, and Interacting on a Virtual Level in Response to the Coronavirus Pandemic. But Don’t Forget to Keep Your Video Conferences Safe Against Intruders During This Difficult Time…

Healthcare providers require top cybersecurity defenses from vendors. A single breach can expose thousands of sensitive and privileged patient records.

Critical vulnerabilities in plugins may put your WordPress site at risk of being breached by cybercriminals. Do you know how to address these potential vulnerabilities?

Here are a few reasons that two-factor authentication will protect your data and enhance your company's cybersecurity measures against hacker intrusions.
![[VIDEO] Five Points: Microsoft Outlook Send Later Feature](https://www.kraftgrp.com/wp-content/uploads/2020/03/Microsoft-Outlook-Send-Later-Feature-336x189.jpg)
Here are a few things you really should know about the Microsoft Outlook Send Later feature found within all recent versions of Microsoft Outlook.